Apr 22, 2023
Unveiling the Underbelly of the Dark Web - Credit Card Fraud

Entering the Mysterious World of the Dark Web
Silk Road, the former online marketplace for drugs, was a prominent feature of the dark web. By using the Tor Browser, it is possible to navigate to various hidden domains within this secretive realm of the internet.
The absence of regulation from authorities or other users provides a simple avenue for cybercriminals to execute fraudulent activities. The Deep Web's Onion provides a comprehensive means of gaining access to the social network through end-to-end encryption.
The TOR network's weaknesses were identified and taken advantage of by the FBI. To determine if someone is trading your information, you must conduct a dark web scan unless you are already on the dark web. Due to the fact that privacy and anonymity are the core of the dark web, it may be assumed that all activities there are illicit.
Monitoring the dark web for any signs of identity theft is a wise move for individuals. Meanwhile, law enforcement agencies keep a close watch on this part of the internet, searching for any stolen data that may provide leads to the culprits of recent security breaches. We encourage readers to share their thoughts and suggestions in the comments section.
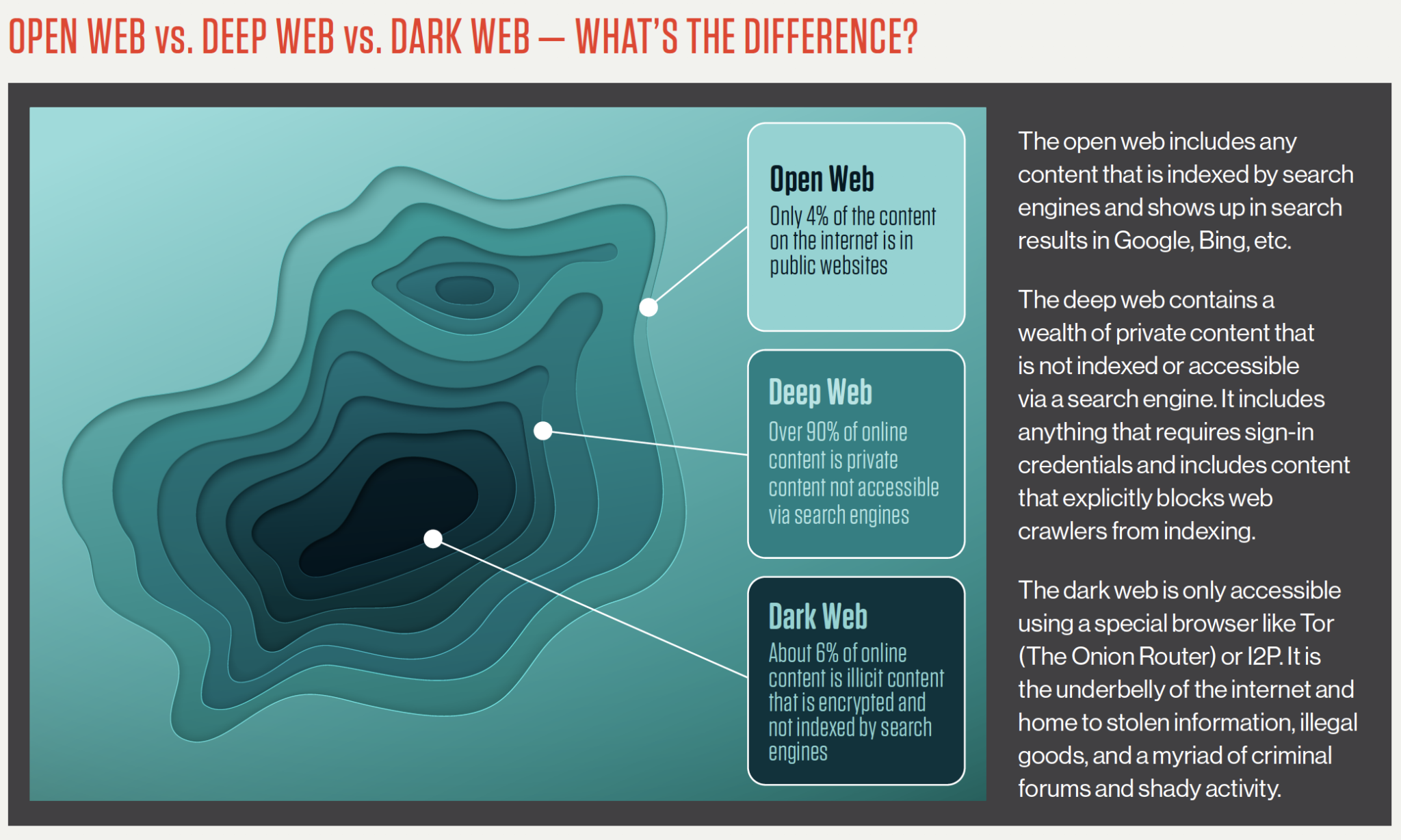
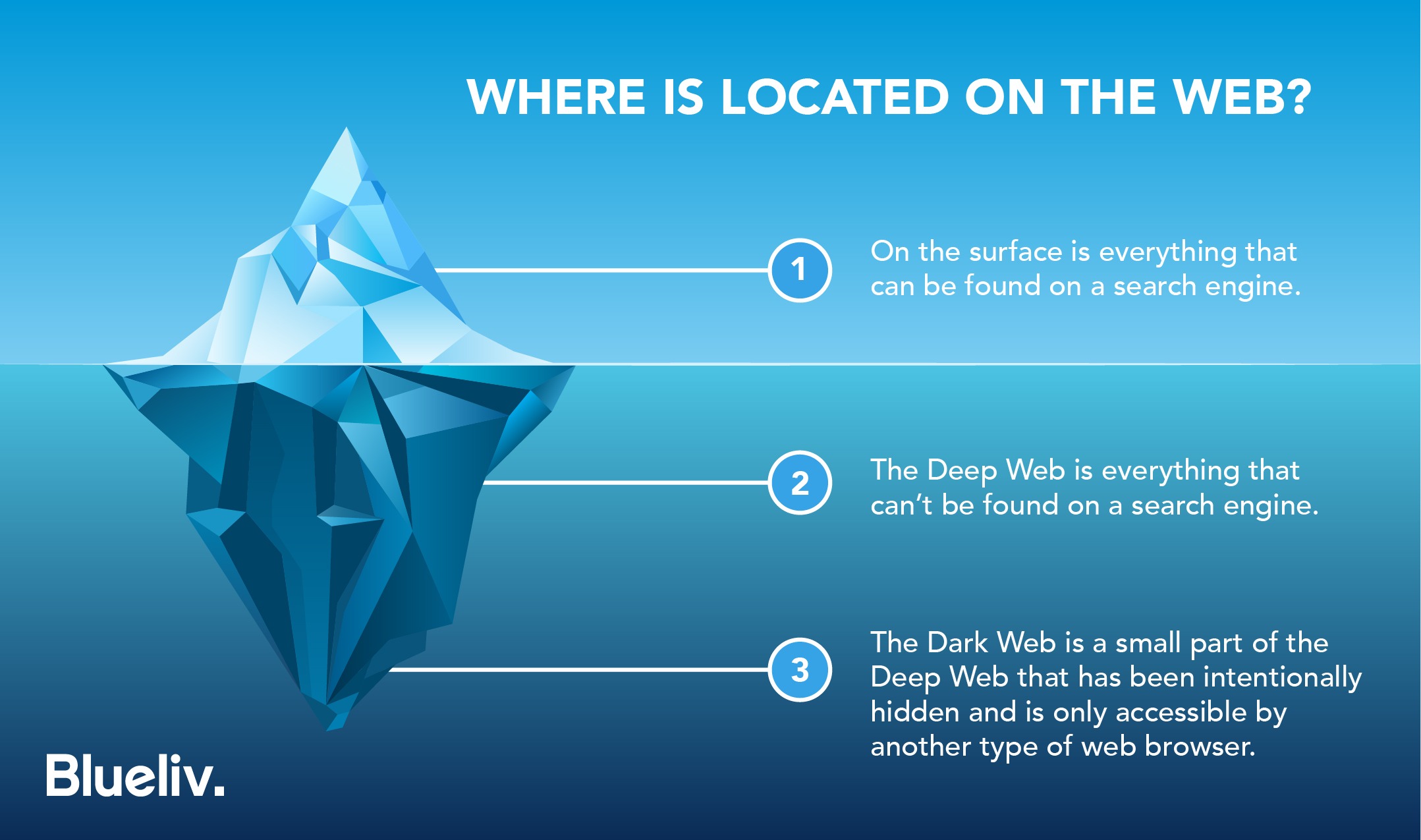
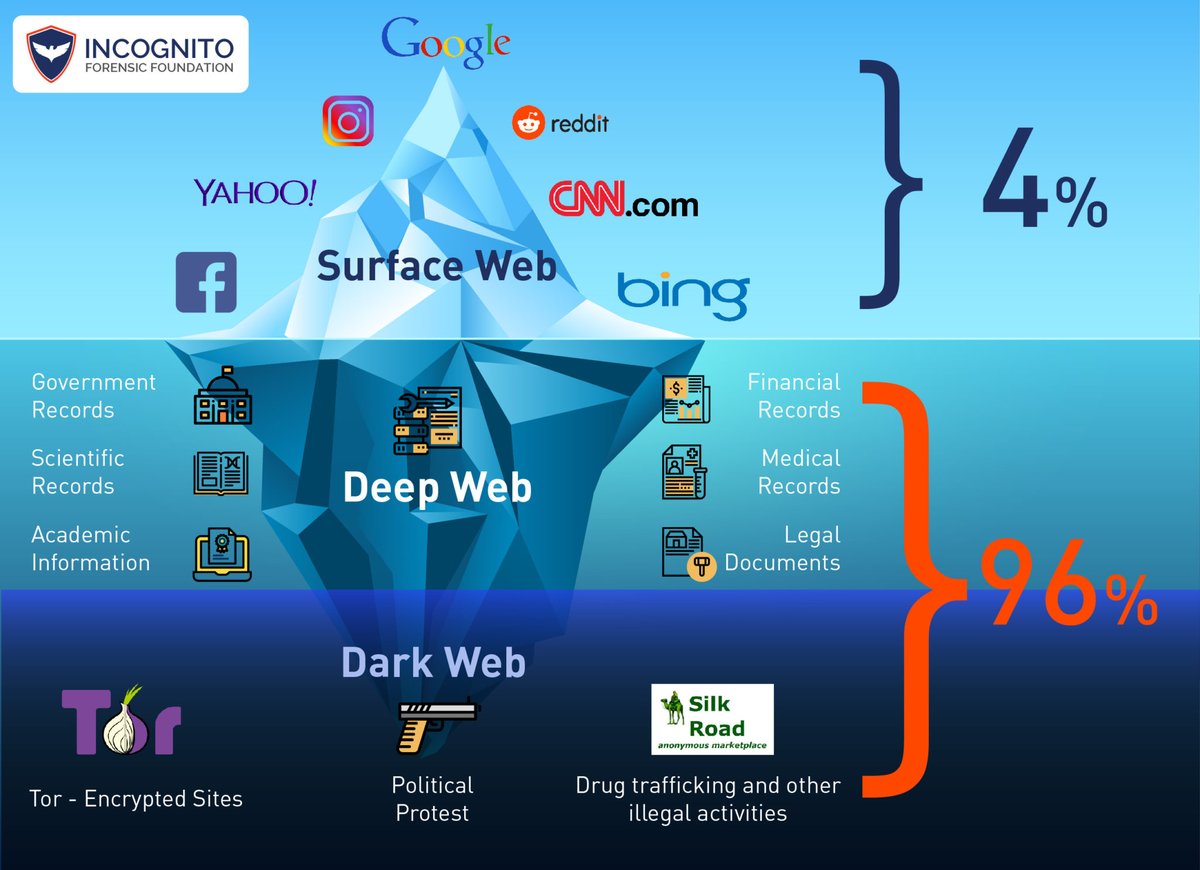
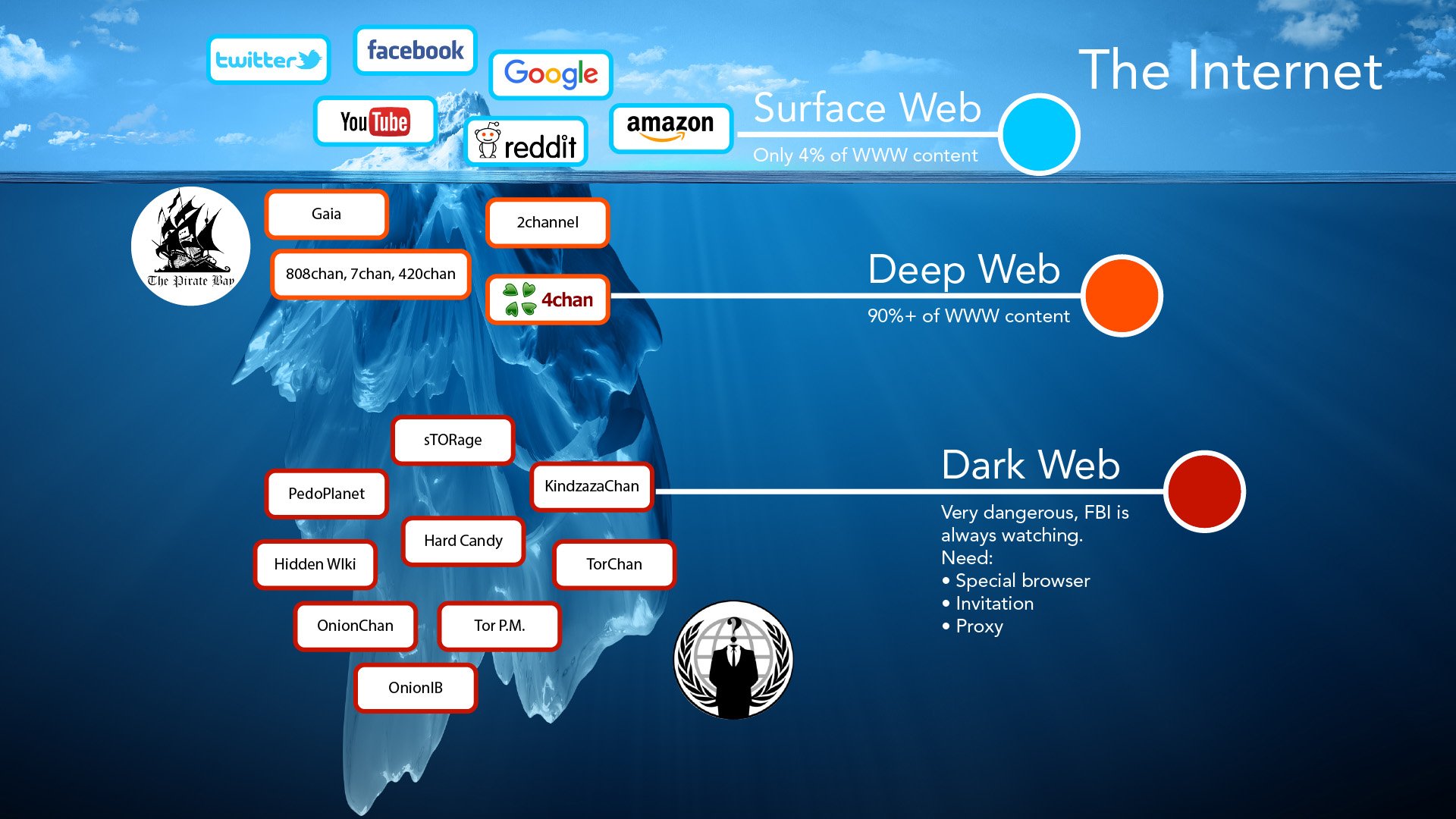
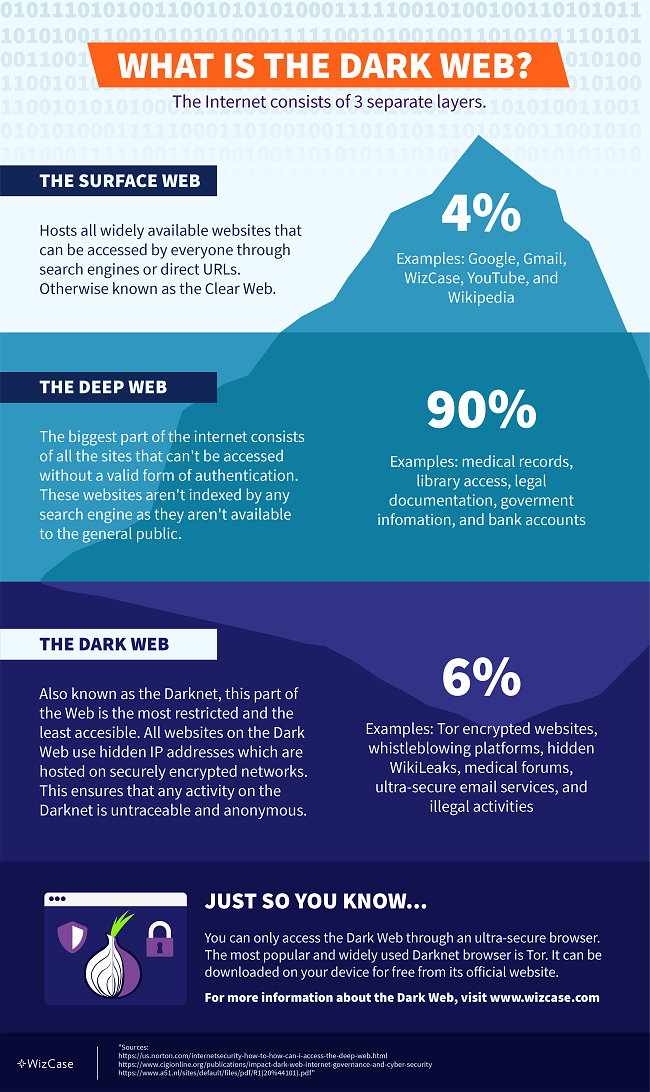
The lower layer of the internet, known as the dark web, is home to a variety of individuals and organizations, including popular web-based enterprises like Facebook, political activists, and journalists who require a secure channel for exchanging confidential data.
Diving into the Depths of the Dark Web
Are your business records present on the Dark Web? To ensure extra security, use a VPN when accessing the dark web or unblocking websites via Tor. Due to its connection with illegal activities, your ISP may monitor your Tor usage, which can attract unnecessary attention to your online activities.
Dark web websites end with .onion instead of .com or .co.
Accessing the dark web allows you to purchase usernames and passwords, as well as view any content that has been blocked from indexing by web crawlers. It is important to note that the dark web differs from the deep web, which includes websites and web pages that are not indexed by search engines, such as login pages and payment portals.
Accessing the dark web can assist in hiding the source of data, thus making it difficult for anyone to trace your IP address. The dark web markets provide an array of lawful and unlawful products. For added safety, it is recommended to route your connection via a VPN and then use the Tor browser to access the dark web, as this combination provides more security than Tor alone.
Accessing the dark web is a matter of personal safety and security preferences.
The Mysterious World of the Silk Road Dark Web
Prior to accessing the dark web, it's crucial to have a clear understanding of the information you seek and the purpose behind logging onto the encrypted network. The ransomware packages are disseminated by the affiliates on the dark web, and the browsing experience is reminiscent of the early days of internet search in the late 1990s.
Accessing the dark web can be a daunting task, as even the most advanced dark web search engines struggle to keep up with the ever-changing terrain.
Accessing the dark web can leave you vulnerable to attacks that involve stealing data from victims and blackmailing them into paying a ransom to avoid having their information released on this hidden part of the internet. To stay safe, follow these step-by-step instructions to determine if you have been compromised. Remember, the first amendment protects your right to access the dark web, but it is important to do so with caution and knowledge of the potential risks.
Avast BreachGuard keeps a constant watch on the dark web to detect data breaches. Since users and vendors remain anonymous, the reliability of any rating system is questionable.
Accessing the Dark Web can be done through the use of specific software such as Tails, which offers users the ability to store encrypted files, run email programs and PGP, and run the TOR browser. In 2020, IBM Security X-Force reported that REvil was involved in 29 of its ransomware engagements.
Explore further
Distributed by Димнур, LLC.