May 03, 2023
Tracking the Shadowy Depths: The Exorbitant Cost of Illegal Drugs on the Black Market

Maintaining a robust IT infrastructure involves maintaining an inventory of assets and consistently managing vulnerabilities. By monitoring the dark web, companies can identify breaches or potential breaches, as well as determine the identity of attackers and the techniques they employ. Certain sectors, such as government, financial institutions, and high-profile IT security firms, may require direct access to intelligence available only through dark web sources, according to Gartner analyst Mitchell Schneider.
Monitoring the dark web is essential in detecting cybercriminals who exploit compromised accounts to launch attacks, perpetrate scams, or carry out spear phishing and brand spoofing campaigns. Protecting high-ranking executives and VIPs is also a priority for Brandefense, as these individuals are not only part of a company's brand but are also frequent targets of attacks. The data available on the dark web includes sensitive information such as SSN, name, date of birth, address, email, phone number, credit card number, password, username, and gender. To take action, access Google One on your computer.
Monitoring the dark web helps you gather crucial information that can be used to prioritize your response according to the level of risk and business requirements. This approach helps to minimize response time and enables faster and more efficient remediation, as each module surfaces actionable intelligence.
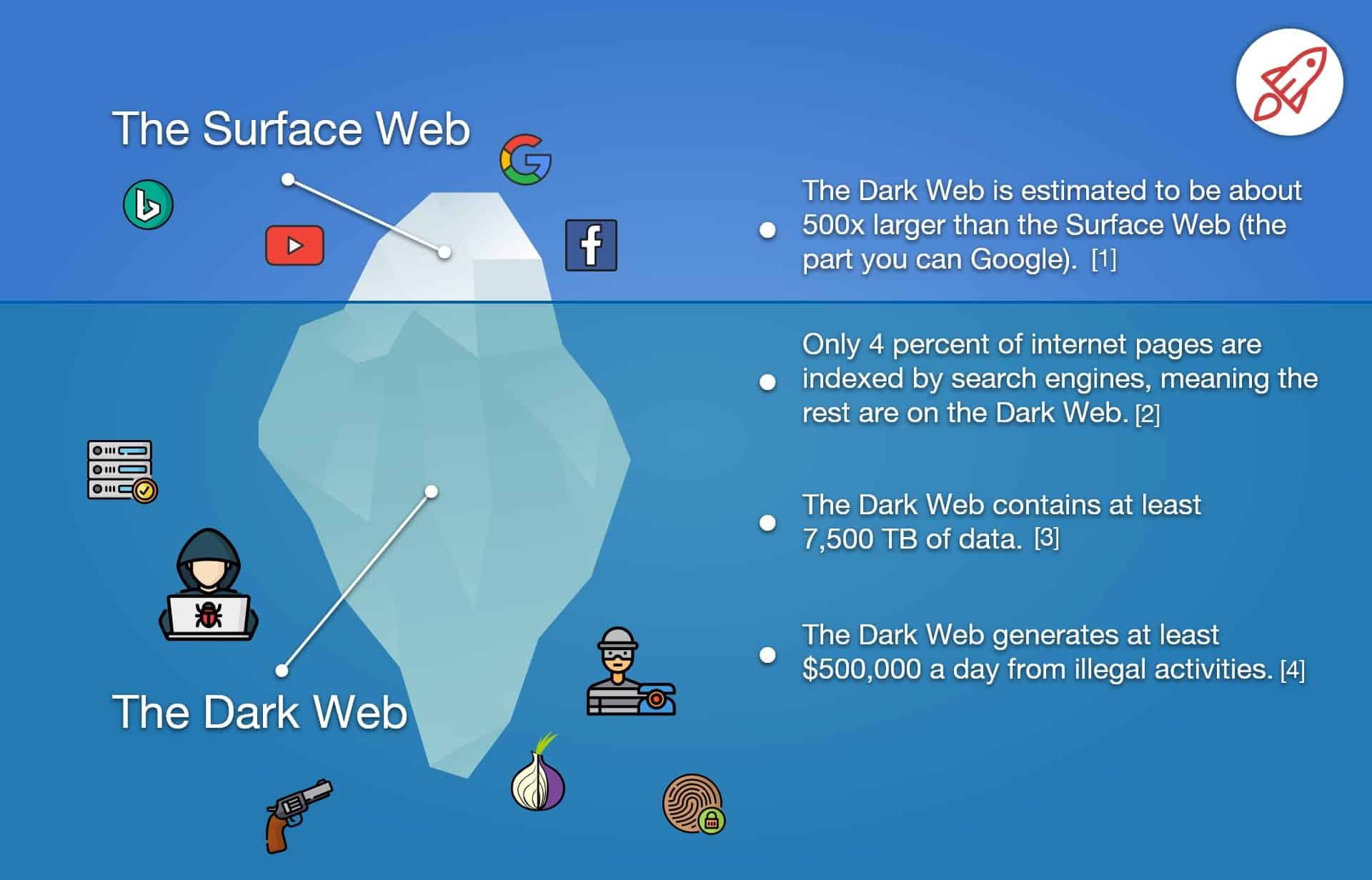
Monitoring the hidden corners of the web: Uncovering onion links
Tracking activities on the dark web is crucial to prevent cyber threats and data breaches. IBM X-Force Exchange offers a comprehensive data sharing platform and community that enables users to access threat and intelligence feeds. This interactive and searchable database can be integrated into existing security systems through APIs and automated alerts. AutoFocus is a vital component of the platform that helps users to monitor and respond to potential cyber threats effectively. To enhance its capabilities, we can explore ways to improve its accuracy and speed in accessing the dark web detecting and analyzing threats, as well as expanding its coverage of the dark web.
Keep a watchful eye on the dark web by monitoring its activities. By doing so, you can stay informed about potential security threats and take appropriate measures to protect your personal information. Utilize tools that allow you to monitor the dark web for any mentions of your name, email, or other sensitive information. This will help you stay proactive against cybercrime and safeguard your online presence.
Monitoring the Dark Web with Mandiant Digital Threat Monitoring provides a comprehensive view of potential threats and exposed confidential information, including leaked credentials and corporate secrets on both the open internet and the dark web. The service is enhanced with augmented dictionaries, which cover colloquial language and slang.
Monitoring the dark web is essential for threat intelligence. It allows threat hunters to expedite their search and gain a more extensive comprehension of the attackers and their tactics. Additionally, it aids in blue teaming efforts to pinpoint and eradicate cybersecurity vulnerabilities and shortcomings.
By keeping an eye on the dark web, you can gather extensive intelligence data that can be processed and analyzed using various tools. This data can be classified and contextualized before being presented to specific modules that focus on different aspects such as your company's brand, potential threats and weaknesses, identities, and other relevant areas.
Tracking Down Phone Numbers on the Dark Web
Monitoring the dark web is crucial for threat hunting. It provides valuable intelligence on threat actors, emerging attack methods, and vulnerabilities. To effectively combat cyber threats, integration of dark web monitoring into security platforms is necessary.
Monitoring the dark web for potential security breaches is crucial to ensure the safety of your personal information. By keeping a close eye on the hidden corners of the internet, you can take proactive measures to prevent cyber attacks and keep your data secure. This is where Google One comes in - offering advanced security features to protect your privacy and keep you in control of your online presence. With Google One, you can rest assured that your personal information is being safeguarded from potential threats, giving you peace of mind in an increasingly digital world.
Monitoring the dark web is a service that is becoming increasingly comprehensive, with different tiers of service available. The simple answer is that everyone can benefit from it.
Out of all the detections that were recorded by CrowdStrike Security Cloud in Q4 of 2021, 62 of them did not contain malware. It is crucial for businesses to take a more proactive approach in response to this. Dark web monitoring tools can provide assistance to both individuals and businesses by actively searching for sensitive information on the dark web, such as proprietary information, trade secrets, and login credentials.
Unveiling the Secret World of Prostitution on the Dark Web
IntSights Threat Intelligence Platform provides comprehensive external threat intelligence and monitoring for indicators of compromise (IOC) on the dark web. To expand the scope of your monitor the dark web monitoring profile and include further personal information from Google Accounts, simply select the relevant checkboxes. OpenCTI, created and owned by Filigran, is a Docker container that can be deployed on any platform and offers a wide range of connectors to other security platforms and software tools for seamless integration and enrichment of the OpenCTI data stream.
Monitoring the dark web is essential to ensure the security of your supply chain and prevent cross-domain attacks that may bypass your current security measures. Trusted partners are monitored to guarantee the safety of your business. The monitoring process involves keeping an eye on millions of websites for targeted information such as corporate email addresses, as well as general data including the company name and industry.
Explore further
Distributed by Абу Мустафа, LLC.